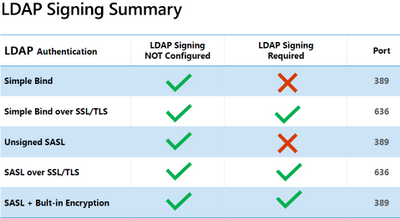
In March 2020, Microsoft is going to release a update which will essentially disable the use of unsigned LDAP which will be the default. This means that you can no longer use bindings or services which binds to domain controllers over unsigned ldap on port 389. You can either use LDAPS over port 636 or using StartTLS on port 389 but it still requires that you addd a certificate to your domain controllers. This hardening can be done manually until the release of the security update that will enable these settings by default.
How to add signed LDAPS to your domain controllers
You can read more about the specific change here –> https://support.microsoft.com/en-us/help/4520412/2020-ldap-channel-binding-and-ldap-signing-requirement-for-windows you can also read more here –> https://techcommunity.microsoft.com/t5/core-infrastructure-and-security/ldap-channel-binding-and-ldap-signing-requirements-update-now/ba-p/921536
After the change the following features will be supported against Active Directory.
How will this affect my enviroment?
Clients that rely on unsigned SASL (Negotiate, Kerberos, NTLM, or Digest) LDAP binds or on LDAP simple binds over a non-SSL/TLS connection stop working after you make this configuration change. This also applies for 3.party solutions which rely on LDAP such as Citrix NetScaler/ADC or other Network appliances, Vault and or authentication mechanisms also rely on LDAP. If you haven’t fixed this it will stop working. This update will apply for all versions.
Windows Server 2008 SP2,
Windows 7 SP1,
Windows Server 2008 R2 SP1,
Windows Server 2012,
Windows 8.1,
Windows Server 2012 R2,
Windows 10 1507,
Windows Server 2016,
Windows 10 1607,
Windows 10 1703,
Windows 10 1709,
Windows 10 1803,
Windows 10 1809,
Windows Server 2019,
Windows 10 1903,
Windows 10 1909
How to check if something is using unsigned LDAP?
If the directory server is configured to reject unsigned SASL LDAP binds or LDAP simple binds over a non-SSL/TLS connection, the directory server will log a summary under eventid 2888 one time every 24 hours when such bind attempts occur. Microsoft advises administrators to enable LDAP channel binding and LDAP signing as soon as possible before March 2020 to find and fix any operating systems, applications or intermediate device compatibility issues in their environment.
You can also use this article to troubleshoot https://docs.microsoft.com/en-us/archive/blogs/russellt/identifying-clear-text-ldap-binds-to-your-dcs
Credits: https://msandbu.org/upcoming-change-microsoft-to-disable-use-of-unsigned-ldap-port-389/