Features on Demand
“Features on Demand (FoD)” is a new concept in Windows 8 that allows administrators and image builders to reduce the amount of space. .
When you install an application that’s ask for .Net Framework 3.5 that will be automatically installed. You don’t have to deploy it automatically with it…
In Windows 8, .Net Framework 3.5 is now a Feature on Demand. And to simplify the installation of common legacy versions of the .Net Framework, .Net 3.0 and 2.0 have been included in the same feature package as 3.5. That means if any of those three versions need to be installed, all the administrator needs to do is enable the single .Net Framework 3.5 feature in Windows 8.
Installation Sources
The .Net Framework 3.5 payload can be obtained from any of the following sources:
· Windows Update (WU)
· A Windows Image file (.wim) to which the payload has been added
· The \sources\sxs folder on the installation media
There are unique advantages to using each. The source can be specified for the environment using a new Group Policy setting. It can also be specified when installing .Net 3.5 manually on an individual machine or image.
The simplest scenario is one in which WU is accessible to both the machine and the user, and the machine is not configured to obtain updates from Windows Server Update Services (WSUS). In this case, when the feature is enabled, the user will be prompted for permission to download the update. If permitted, Windows will download the payload directly from Windows Update and install the feature. Done!
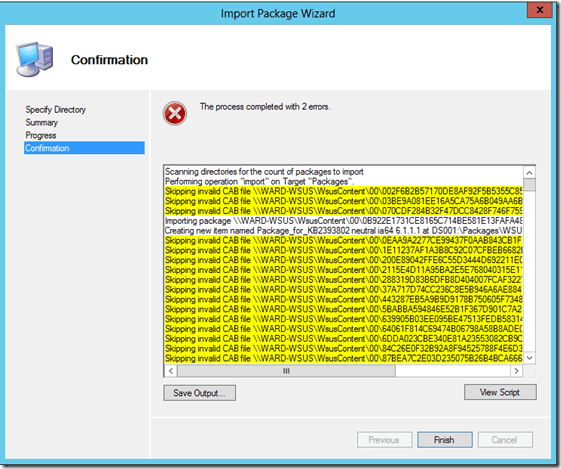
In more controlled environments, administrators might want to redirect such download requests to an alternate source such as a Windows Image file (.wim) to which the payload was added, or the\sources\sxs folder from the installation media. There might also be network , proxy, or security configurations that prevent users from directly accessing Windows Update. Additionally, WSUS does not currently support the payloads for Features on Demand, although it does support the subsequent patching of the features. So in environments where machines are configured to obtain updates from WSUS, administrators will need to configure the source for initial FoD installations.
To allow administrators to manage these scenarios, a new Group Policy setting was introduced in Windows 8 / Windows Server 2012: “Specify settings for optional component installation and component repair”, located under Computer Configuration\Administrative Templates\System:

This policy allows the administrator to configure the installation of Features on Demand and feature store repair operations to use only authorized locations.
When this policy is enabled, a network location (for example, a file server) can be specified for both repair of the feature store, and enabling features whose payloads were not originally added. The Alternate source file path can point to a \sources\sxs folder or a Windows image (WIM) file using the WIM: prefix. The repair WIM can be different than the initial WIM file used for installation. You can specify multiple paths by using “;” between the paths. Valid syntax is “wim:<path to wim>:<index>”. Or “<path to sxs folder>”.
Examples:
\\server\Win8Media\sources\sxs
wim:\\server\sourcewim\install.wim:3
If you select Never attempt to download payload from Windows Update, WU is not contacted during an installation or repair operation.
If you select Contact Windows Update directly to download repair content instead of Windows Server Update Services (WSUS), attempts to add features (for example, .NET Framework 3.5) or repair the feature file store use Windows Update to download files. Target computers require Internet and WU access for this option. Normal servicing operations continue to use WSUS if it has been configured as a source.
Like this:
Like Loading...
![]()